Basic and Fundamental Concepts of Crypto Wallets
This post is designed to improve your understanding of the core principles behind crypto wallets, focusing on the role and function of mnemonic phrases, private keys, public keys, and wallet addresses. Perfect for beginners seeking clarity on how wallet security and access work in the world of blockchain.
WALLETS
Pedro Machado
5/12/20254 min read


Introduction
Understanding how crypto wallets work is essential for anyone stepping into the world of blockchain. In this post, we’ll break down the fundamental components — from mnemonic phrases to private and public keys — and explain how they come together to create secure wallet addresses. Let’s demystify the basics so you can navigate your crypto journey with confidence.
Wallets
Crypto wallets are applications designed for various environments—such as browsers, desktops, or even mobile devices—that allow users to manage the funds associated with a stored key pair. These applications provide an interface for sending and receiving cryptocurrencies, signing transactions, and managing the private keys required to access these funds. Wallets can be classified into different types, including software wallets, hardware wallets, and online wallets, each with its own features and security considerations. Choosing the right wallet that fits your needs and offers a high level of security is essential to protect your digital assets, such as ERC20 tokens and NFTs.
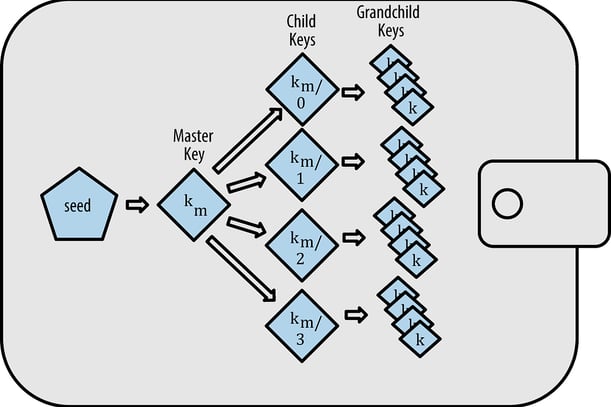
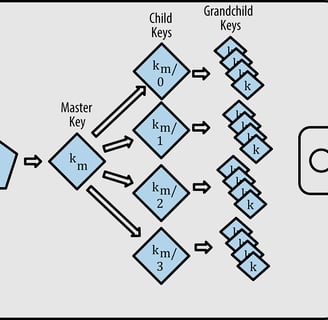
Hierarchical Deterministic Wallets (HD Wallets)
Today, the most commonly used types of wallets—due to their ease of use, portability, multi-chain and multi-asset support—are Hierarchical Deterministic Wallets, or HD Wallets. These wallets are derived from a seed, which can be encoded as a mnemonic phrase. From this seed, a master key is generated, and from that master key, a tree-like structure of child keys is derived.
HD Wallets use a standardized derivation path to classify and organize wallet keys, typically following the format:
m / purpose' / coin_type' / account' / change / address_index
This path defines a wallet container. For example, in the case of Ethereum, a valid path could be m/44/0/0/1, which refers to the private key at index 1 of account 0. This type of wallet allows users to manage multiple addresses and transactions within a single application, simplifying the handling of various cryptocurrencies through one unified interface. This type of wallet, which allows users to manage multiple addresses and transactions within a single application, is implemented by popular applications like MetaMask and Trust Wallet.
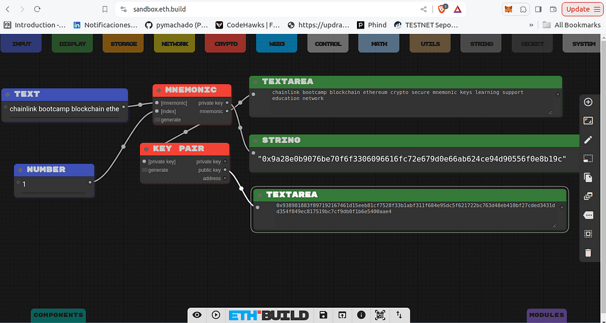
Mnemonic Phrase
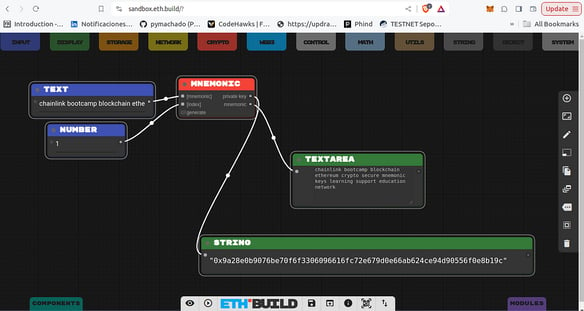
The mnemonic phrase, or a set of human-readable words, encodes the seed of a deterministic wallet. This allows users to recover or regenerate all derived key pairs from a single backup. It is absolutely crucial to store this phrase securely and never share it — exposing it could compromise all the funds associated with the derived keys.
Example:
chainlink bootcamp blockchain ethereum crypto secure mnemonic keys learning support education network
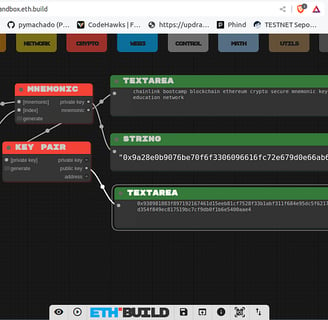
Private Key
A private key is simply a large integer. In theory, this could be any number — even something as simple as 1, your national ID number, or your birth date. However, for cryptographic security, the private key must be a 256-bit randomly generated number.
For example, if you flip a coin 256 times and record heads as 0 and tails as 1, you will end up with a unique, random 256-bit binary number that can be used as a secure private key.
You can see how to derive a private key from the mnemonic phrase above by clicking here.
Public Key
The public key is derived from the private key using the Elliptic Curve Multiplication algorithm — a one-way mathematical process. This means that while you can generate a public key from a private key, it is computationally infeasible to reverse the process and determine the private key from the public key.
You can view an example of how to derive a public key from the private key mentioned above by clicking here.
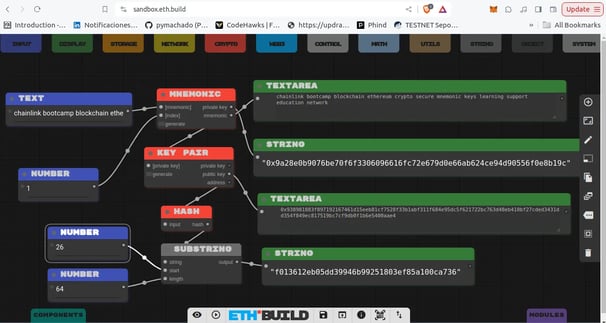
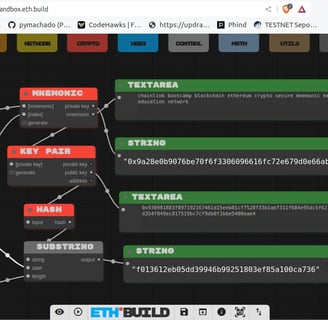
Address
In Ethereum, the address is derived from the last 20 bytes (or final 160 bits) of the hash of the public key. This address is used as the public identifier that can be shared with others on the network for sending assets or data to the associated wallet.
You can see an example of how to derive an address from the public key mentioned above by clicking here.
Conclusion
In conclusion, we’ve explored the fundamental concepts of crypto wallets, focusing on the importance of the mnemonic phrase, private key, public key, and wallet address. These elements are critical to the security and functionality of blockchain wallets. Understanding how they interact empowers users to protect their digital assets and manage transactions effectively.
It is essential to keep both the mnemonic phrase and private key strictly confidential, while the public key and wallet address serve as secure and verifiable identifiers for receiving and validating transactions on the blockchain network.
Recommendation
We recommend watching the video “Public Key Cryptography” by Pedro Machado on the Blockitus YouTube channel. This video provides a clear and accessible explanation of the role of public key cryptography in blockchain, complementing the concepts introduced in this article.
📺 You can find the video at this link.
To explore the topic of HD Wallets in more depth, we also recommend consulting the book.
Innovate
Empowering a Decentralized Future Through Cutting-Edge Technologies and Human Collaboration.
Engage
